Understanding AES: The Advanced Encryption Standard
An overview of the Advanced Encryption Standard (AES) and its implementation across various platforms.
Introduction
The Advanced Encryption Standard (AES), introduced by the National Institute of Standards and Technology (NIST) in 2001, is a robust symmetric encryption algorithm derived from the Rijndael cipher family. AES supports three key sizes—128, 192, and 256 bits—and uses a single key for both encryption and decryption. Unlike asymmetric encryption, which requires two keys, AES simplifies security by relying on one secret key. Originally developed for U.S. government use, AES is now globally recognized as one of the most secure and widely adopted encryption standards. 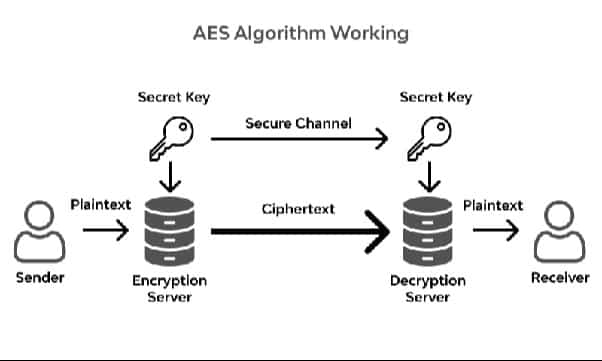
Why Was AES Developed?
The Data Encryption Standard (DES), established in the 1970s, became vulnerable over time due to its 64-bit key size (56 usable bits), making it susceptible to brute-force attacks. To address these limitations, NIST initiated a search for a new encryption standard in 1997, inviting global cryptographic submissions. The Rijndael algorithm was selected for its strong security and efficiency, operating on 128-bit data blocks. AES is now a widely accepted standard, published by NIST and used in various regulatory frameworks.
Understanding Key Size Differences
AES encrypts data in 128-bit blocks using keys of 128, 192, or 256 bits. Larger keys provide greater security:
| Specification | AES-128 | AES-192 | AES-256 |
|---|---|---|---|
| Key Length (bits) | 128 | 192 | 256 |
| Number of Rounds | 10 | 12 | 14 |
| Key Schedule Size | 176 bytes | 208 bytes | 240 bytes |
| Encryption Strength | Moderate | Higher | Strongest |
The number of rounds increases with key size, enhancing security. While 256-bit keys offer the highest protection, 128-bit keys are sufficient for most applications.
How AES Works
AES is a symmetric block cipher that transforms plaintext into ciphertext through several steps:
- Key Expansion: The secret key is expanded to generate round keys.
- Initial Round: Each byte of the data block is XORed with the round key.
- Rounds (10, 12, or 14 depending on key size):
- SubBytes: Non-linear substitution using an S-box.
- ShiftRows: Transposition by shifting rows.
- MixColumns: Mixing operation for diffusion.
- AddRoundKey: XOR with the round key.
- Final Round: Similar to previous rounds but omits MixColumns.
- Decryption: The process is reversed using the same round keys.
Example
Encrypting the message “CONFIDENTIAL” with AES-256:
- Key Generation: Create a strong 256-bit key.
- Encryption: Apply 14 rounds of AES transformations.
- Ciphertext: The result is a random-looking string, e.g., “X1Y2Z3…”.
The recipient uses the same key to decrypt and recover the original message. AES-256 ensures that brute-force attacks are computationally infeasible.
Where Can AES Be Implemented?
AES is used in a wide range of applications:
- VPNs (e.g., PureVPN): Secures internet traffic.
- Password Managers (e.g., Keeper): Protects stored passwords.
- Mobile Apps & Wireless Networks: Encrypts sensitive data.
- Video Games: Prevents piracy by encrypting game assets.
- Hard Drives & Messaging Apps: Secures stored and transmitted data.
- Programming Libraries: Available in Java, Python, C++, and more.
- File Compression & Browsers: Ensures data privacy.
Advantages and Disadvantages
| Advantage | Disadvantage |
|---|---|
| Globally recognized and widely adopted standard | AES-256 can be computationally intensive |
| Advanced security against cryptographic attacks | Security depends on proper key management |
| Versatile for various applications | Quantum computing may pose future risks |
| Flexible key sizes for different security needs | Vulnerable to side-channel attacks if not properly implemented |
| NIST-approved for government and private-sector use | Key setup and distribution can be challenging in large systems |
Comparison: AES vs. Triple-DES vs. DES
| Feature | DES | Triple-DES | AES |
|---|---|---|---|
| Full Name | Data Encryption Standard | Triple Data Encryption Algorithm | Advanced Encryption Standard |
| Year Introduced | 1976 | 1998 | 1999 |
| Key Length | 56 bits (weak) | 112 or 168 bits (112 bits secure) | 128, 192, or 256 bits |
| Block Size | 64 bits | 64 bits | 128 bits |
| Security | Weak, brute-forceable | More secure than DES, but less than AES | Strong, no known successful attacks |