Buffer Overflow - Part 02
A concise primer on stack-based buffer overflows covering exploitation techniques, common mitigations, and defensive best practices.
Beyond the Basics: Exploiting the Stack with Buffer Overflows
If basic hacking is like picking a lock, Buffer Overflow Exploitation is like having the blueprints for the building’s support structure and knowing exactly where to plant the explosives. It’s one of the most fundamental, yet advanced, topics in the OSCP (Offensive Security Certified Professional) syllabus, serving as a rite of passage for every serious offensive security practitioner.
Why? Because it forces you to understand computer memory, assembly language, and program execution flow—the deep mechanics that underpin nearly all software. It’s pure, hands-on exploit development.
What is a Buffer Overflow, Anyway?
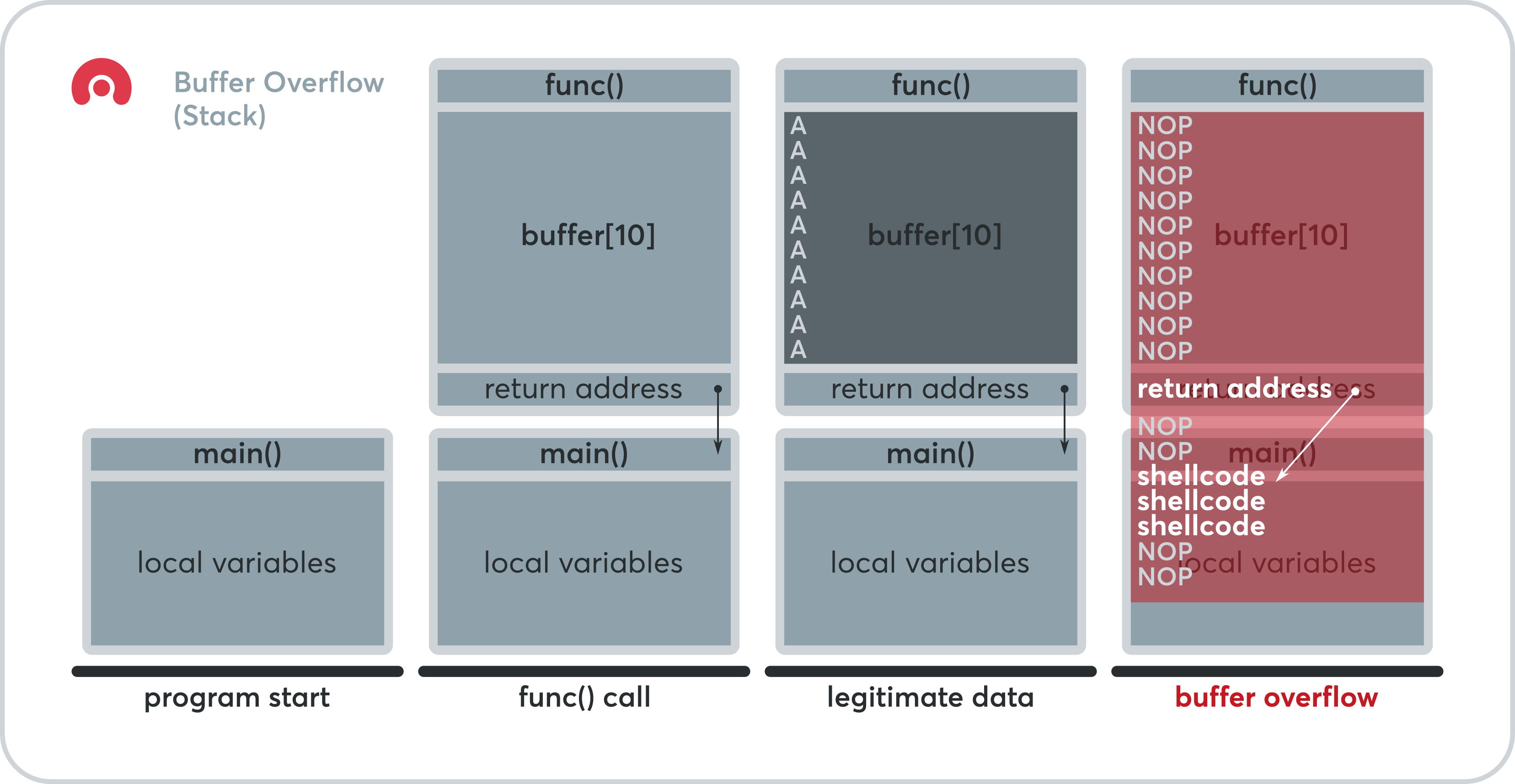
Imagine you have a small coffee cup (the buffer) designed to hold 8 ounces. A helpful but careless friend (the vulnerable program) tries to pour 12 ounces of coffee (the input data) into it.
What happens? The excess 4 ounces overflows and spills onto the surrounding desk space (the adjacent memory).
In a software program, this adjacent memory often holds critical information, most importantly, the Return Address. This is the pointer telling the program what instruction to execute next when it finishes its current task. By overflowing the buffer, an attacker can overwrite this return address with the memory location of their own malicious code (the Shellcode).
- Goal: Hijack the program’s execution flow.
- Result: The program executes the attacker’s code instead of its intended next instruction, often leading to a remote shell or gaining full control of the system.
The Anatomy of an OSCP-Style Exploit 🔬
The OSCP focuses heavily on stack-based buffer overflows, particularly on older 32-bit Windows systems, because they are the cleanest way to teach the core concepts. The process isn’t just one step; it’s a methodical, six-step dance:
1. Fuzzing: Finding the Crash Point
You start by blindly sending increasing amounts of data (often just the letter ‘A’ repeated) to the vulnerable application until it crashes. This tells you roughly how many bytes it takes to completely fill the buffer and overwrite the critical memory area.
2. Finding the Exact Offset
Once you have a crash, you use a special, non-repeating pattern (a De Bruijn sequence) to identify the precise byte that overwrites the Extended Instruction Pointer (EIP) register. This register holds the overwritten Return Address, and knowing its exact position (the Offset) is crucial.
3. Identifying Bad Characters
Programs often filter or handle certain bytes in a way that breaks your shellcode. You systematically test for these “Bad Characters” (like null bytes or carriage returns) and ensure they are removed from your final payload.
4. Locating a Jump Point
You need a reliable, hardcoded address in the program’s memory to jump to, which will then direct the execution to your shellcode. The most common instruction is JMP ESP (Jump to Stack Pointer), found in non-protected DLLs. This instruction effectively redirects the program to the start of your injected payload on the stack.
5. Generating and Staging Shellcode
The Shellcode is the small, highly optimized code that performs the attacker’s ultimate goal—usually spawning a reverse shell back to your Kali Linux machine. You generate this payload, ensuring it avoids the bad characters found earlier.
6. Final Execution!
You combine all the pieces into a single, Python-scripted exploit:
\[[\text{Junk}] + [\text{EIP (JMP ESP Address)}] + [\text{NOP Sled}] + [\text{Shellcode}]\]The script sends this payload, the vulnerable program runs, the overflow occurs, the EIP is overwritten, and the program is redirected to your shellcode. Congratulations—you’ve achieved Remote Code Execution (RCE).
Why This Matters in Advanced Defense
While modern operating systems have strong defenses like DEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization) to mitigate classic stack overflows, understanding the mechanism is still vital:
- Legacy Systems: Older systems, embedded devices, and IoT hardware often lack these modern protections, making buffer overflows an immediate, high-impact threat.
- Fundamental Skill: Exploit development is a core skill for advanced defensive research. If you can write an exploit, you know how to fix a vulnerability, making you a better security engineer.
- Defense-in-Depth: Modern attacks often use complex variations like Return-Oriented Programming (ROP) to bypass DEP and ASLR. Learning the basics of the stack is the starting point for understanding these advanced defenses and bypass techniques.
It’s about understanding the machine at its most granular level. In cybersecurity, that deep knowledge is the real power.