The CIA Triad: Foundation of Information Security
A comprehensive guide to understanding the CIA Triad and Parkerian Hexad.
Understanding the CIA Triad in Information Security
The CIA Triad is a foundational concept in information security, representing three core attributes that define what it means to protect information: Confidentiality, Integrity, and Availability. These elements are essential considerations when developing security strategies and defenses. While not every security measure addresses all three properties equally, each plays a critical role in maintaining a balanced and effective security posture.
The CIA Triad: An Overview
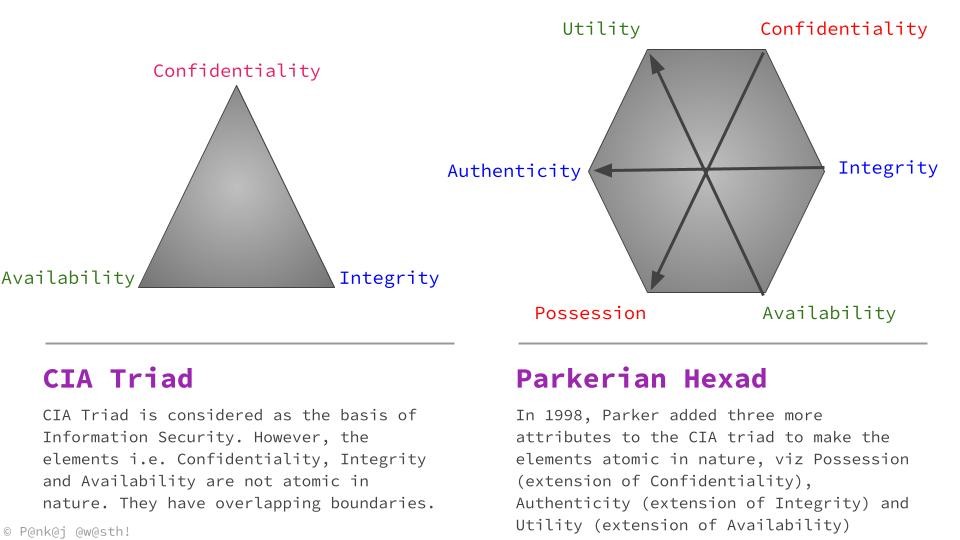
The triad is often depicted as an equilateral triangle, symbolizing that each property holds equal importance. If any side is compromised, the triangle—and thus the security of your organization—is broken. The three elements are:
- Confidentiality
- Integrity
- Availability
Let’s explore each component in detail.
1. Confidentiality
Confidentiality is about keeping information secret and ensuring that only authorized individuals have access to sensitive data. In both personal and digital contexts, breaches of confidentiality can erode trust and lead to significant consequences.
Key aspects of confidentiality:
- Access Control: Restricting data access to authorized users.
- Encryption: Protecting data at rest (stored) and in motion (transmitted) using technologies like SSL/TLS.
- Password Security: Using strong, unique passwords to prevent unauthorized access.
Example:
If you share a secret with a friend and they tell someone else, your trust is broken—confidentiality has been breached. In the digital world, if an attacker gains access to your encryption keys, they can decrypt and access your confidential data.
2. Integrity
Integrity ensures that information remains accurate and unaltered from its original state, whether during storage or transmission. Loss of integrity can occur due to accidental corruption, hardware failures, or malicious attacks.
Ways integrity can be compromised:
- Data Corruption: Hardware issues (e.g., faulty memory or disks) can alter data.
- Human Error: Overwriting or mistakenly editing important documents.
- Man-in-the-Middle Attacks: Attackers intercept and modify data in transit.
Example:
If you send a document and it is altered before reaching the recipient, or if a digital signature is forged, the integrity of the information is compromised.
3. Availability
Availability means that information and services are accessible to authorized users when needed. Failures in availability can result from technical issues, misconfigurations, or deliberate attacks.
Common threats to availability:
- Hardware Failures: Forgetting an external drive or losing access to storage.
- Misconfiguration: Changes to system settings that prevent services from running.
- Denial-of-Service (DoS) Attacks: Overwhelming a service with traffic to make it unavailable to legitimate users.
Example:
If a critical service goes down due to a configuration error or a DoS attack, users cannot access the resources they need, resulting in a breach of availability.
Beyond the Triad: The Parkerian Hexad
Some experts argue that the CIA Triad does not fully encompass all aspects of information security. In 1998, Donn Parker proposed the Parkerian Hexad, adding three more properties:
- Possession (or Control): Who physically or logically controls the data.
- Authenticity: Assurance that data is from a genuine source (sometimes called nonrepudiation).
- Utility: The usefulness of data—data may be available but unusable due to format or lack of compatible hardware.
Examples:
- Possession: If you hand your external drive to a friend by mistake, you lose control, even if confidentiality isn’t breached.
- Authenticity: Digital signatures help verify the sender, but if keys are stolen, authenticity is compromised.
- Utility: Data stored on obsolete media (like a nine-track tape) may be technically available but practically useless.
While these additional properties highlight specific scenarios, many can be mapped back to the original triad. For instance, possession and utility often relate to availability, while authenticity ties into integrity.
Conclusion
The CIA Triad—Confidentiality, Integrity, and Availability—forms the backbone of information security. Understanding and balancing these properties is crucial for protecting organizational assets. While extended models like the Parkerian Hexad offer more granularity, the triad remains a practical and widely adopted framework for assessing and implementing security controls.