How DES Encryption Was Broken
A technical overview of the Data Encryption Standard (DES), its vulnerabilities, and how it was ultimately broken.
How DES Encryption Was Broken
The Data Encryption Standard (DES) was once the cornerstone of symmetric-key cryptography, adopted as a federal standard in 1977. However, over time, advances in computing and cryptanalysis exposed critical weaknesses, leading to its deprecation.
Technical Overview: What Is DES?
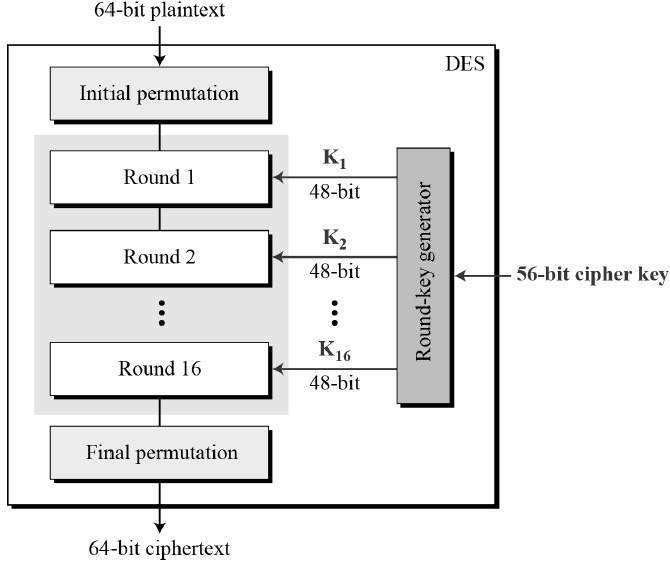
- Block Cipher: DES is a symmetric block cipher that encrypts data in 64-bit blocks using a 56-bit key.
- Feistel Structure: It uses 16 rounds of Feistel network operations, combining substitution and permutation steps.
- Widespread Adoption: DES was widely used in banking, government, and commercial applications for decades.
Why Was DES Considered Secure?
At the time of its adoption, brute-forcing a 56-bit key was computationally infeasible. The algorithm’s internal structure was also designed to resist known cryptanalytic attacks of the era.
How DES Was Broken
1. Brute-Force Attacks
- Keyspace Limitation: With only 56 bits of key material, DES has 2⁵⁶ possible keys (~72 quadrillion).
- Hardware Advances: By the late 1990s, specialized hardware made exhaustive key search practical.
- Notable Event: In 1998, the Electronic Frontier Foundation (EFF) built the “DES Cracker,” a machine that could search the entire DES keyspace in about 56 hours. Later optimizations reduced this to under 24 hours.
2. Cryptanalytic Attacks
- Differential Cryptanalysis: While DES was designed to resist this attack, later research showed that with enough chosen plaintexts, it could be vulnerable.
- Linear Cryptanalysis: Introduced in the early 1990s, this technique could recover the key faster than brute force, though still requiring vast amounts of data.
3. Real-World Implications
- Banking and Commerce: The feasibility of breaking DES meant that sensitive financial transactions were at risk.
- Transition to Stronger Algorithms: The vulnerabilities led to the adoption of Triple DES (3DES) and, eventually, the Advanced Encryption Standard (AES).
Lessons Learned
- Key Length Matters: DES’s 56-bit key is now considered far too short for modern security needs.
- Moore’s Law: Advances in hardware continually reduce the time required for brute-force attacks.
- Algorithm Agility: Cryptographic systems must be designed to allow for rapid upgrades as new attacks emerge.
Demo: Brute-Forcing DES in Python
Below is a simple Python script that demonstrates a brute-force attack on DES. For demonstration, the keyspace is limited to 16 bits (not secure) to keep the runtime reasonable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
from Crypto.Cipher import DES
import itertools
def pad(text):
while len(text) % 8 != 0:
text += b' '
return text
# Known plaintext and ciphertext
plaintext = b"secret!!"
key = b"key00000" # 8 bytes (for demo)
cipher = DES.new(key, DES.MODE_ECB)
ciphertext = cipher.encrypt(pad(plaintext))
# Brute-force search (only 16 bits for demo)
def brute_force_des(ciphertext, known_plaintext):
for k in range(2**16):
test_key = k.to_bytes(2, 'big') + b'\x00'*6
test_cipher = DES.new(test_key, DES.MODE_ECB)
decrypted = test_cipher.decrypt(ciphertext).strip()
if decrypted == known_plaintext:
print(f"Key found: {test_key.hex()}")
return test_key
print("Key not found.")
brute_force_des(ciphertext, plaintext)
Note: Real DES uses a 56-bit key, making brute-force infeasible without massive resources. This demo is for educational purposes only.
Conclusion
DES played a foundational role in the history of cryptography, but its eventual defeat underscores the importance of strong key management and ongoing cryptanalysis. Today, DES serves as a cautionary tale and a milestone in the evolution of encryption standards.