SHA-256 Explained
A comprehensive guide to SHA-256, the most widely used hashing algorithm
SHA-256 Explained
SHA-256 (Secure Hash Algorithm 256-bit) is a cryptographic hash function that converts input data into a fixed-length 256-bit string. It is widely used in blockchain, digital signatures, and password hashing to protect data from tampering and unauthorized access.
What is SHA-256?
- SHA (Secure Hash Algorithm): A set of cryptographic functions that transform data into a fixed-size, seemingly random string.
- 256-bit: The output length of the hash, always 256 bits regardless of input size.
SHA-256 ensures that even a minor change in input data generates a completely different hash, making it a reliable tool for verifying data integrity and securing sensitive information. It is part of the SHA-2 family, developed by the NSA.
How SHA-256 Works
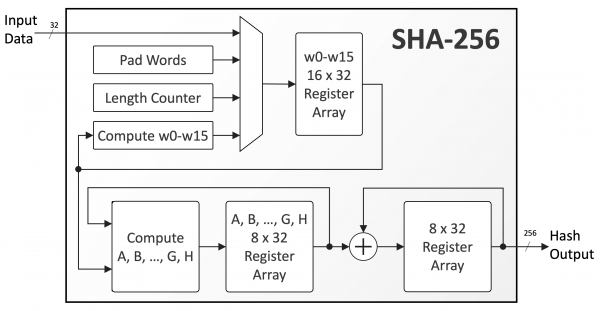
SHA-256 processes data through several steps to produce a unique, fixed-size hash:
- Input Preparation
- Pads the input data so it fits into fixed-size chunks (512 bits).
- Padding involves adding a ‘1’ bit, followed by enough ‘0’s, and a bit indicating the original length.
- Initial Setup
- Uses predefined constants as starting hash values, derived from the square roots of the first eight prime numbers.
- Processing the Data in Blocks
- Splits the padded data into 512-bit blocks.
- Each block is divided into 16 chunks of 32 bits, then expanded to 64 chunks using logical operations.
- Compression Function
- Processes each block in 64 rounds using bitwise operations (AND, OR, XOR), modular addition, and bit shifts.
- Ensures even a small input change drastically alters the output.
- Producing the Final Hash
- After all blocks are processed, the final 256-bit hash is produced—a unique digital fingerprint of the input.
Security Aspects of SHA-256
Cryptographic Properties
- Collision Resistance: Extremely difficult to find two different inputs with the same hash.
- Pre-image Resistance: Hard to reverse-engineer the original input from its hash.
- Second Pre-image Resistance: Challenging to find a different input with the same hash as a given input.
Resistance to Attacks
- Length Extension Attack: SHA-256 is susceptible, but using HMAC mitigates this risk.
- Brute Force Attacks: Impractical due to the astronomical number of possible 256-bit hashes.
Quantum Computing
- SHA-256 is currently secure against quantum attacks, but research into quantum-resistant algorithms is ongoing.
Why SHA-256 Is Trusted
- Used globally in critical applications (internet security, digital currencies, etc.).
- Extensively scrutinized and recommended by organizations like NIST.
- Trusted due to its robust cryptographic properties and resistance to common attacks.
Real-World Applications
Bitcoin and Cryptocurrencies
- Used for transaction hashing and proof-of-work mining.
- Ensures blockchain security and prevents fraud.
SSL/TLS Certificates
- Verifies the integrity and authenticity of certificates.
- Protects against man-in-the-middle attacks.
Software Distribution
- Developers provide SHA-256 hashes for downloads.
- Users verify file integrity by comparing hashes.
Data Integrity and Verification
- Used in cloud storage and data transmission to ensure files remain unaltered.
Digital Signatures
- Hashes documents before signing.
- Ensures authenticity and integrity of electronic documents.
Case Study: U.S. Federal Government
- Mandates SHA-256 for securing sensitive information and authenticating users.
Comparisons with Other Hashing Algorithms
SHA-256 vs SHA-1
- SHA-1: 160-bit hash, now deprecated due to collision vulnerabilities.
- SHA-256: 256-bit hash, stronger security, recommended for modern applications.
SHA-256 vs SHA-3
- SHA-3: Uses Keccak construction, resistant to different attacks.
- Both can produce 256-bit hashes; SHA-256 remains more widely adopted.
SHA-256 vs MD5
- MD5: 128-bit hash, obsolete due to security flaws.
- SHA-256: No known practical vulnerabilities, much higher security.
Future of SHA-256
- Ongoing Research: Continual analysis to identify vulnerabilities.
- Quantum Computing: Potential future threat, but SHA-256 is currently secure.
- Transition to SHA-3: May occur in specific applications requiring extra security.
- Continued Adoption: Widespread use and integration ensure ongoing relevance.
- Education and Best Practices: Promoting secure implementation and awareness.
- Evolving Standards: NIST and others update guidelines as technology advances.
Bottom Line
SHA-256 is a pillar of modern cryptographic security, vital for protecting digital information. Its robustness, versatility, and ongoing scrutiny ensure its continued role in safeguarding data, even as new technologies and standards emerge.