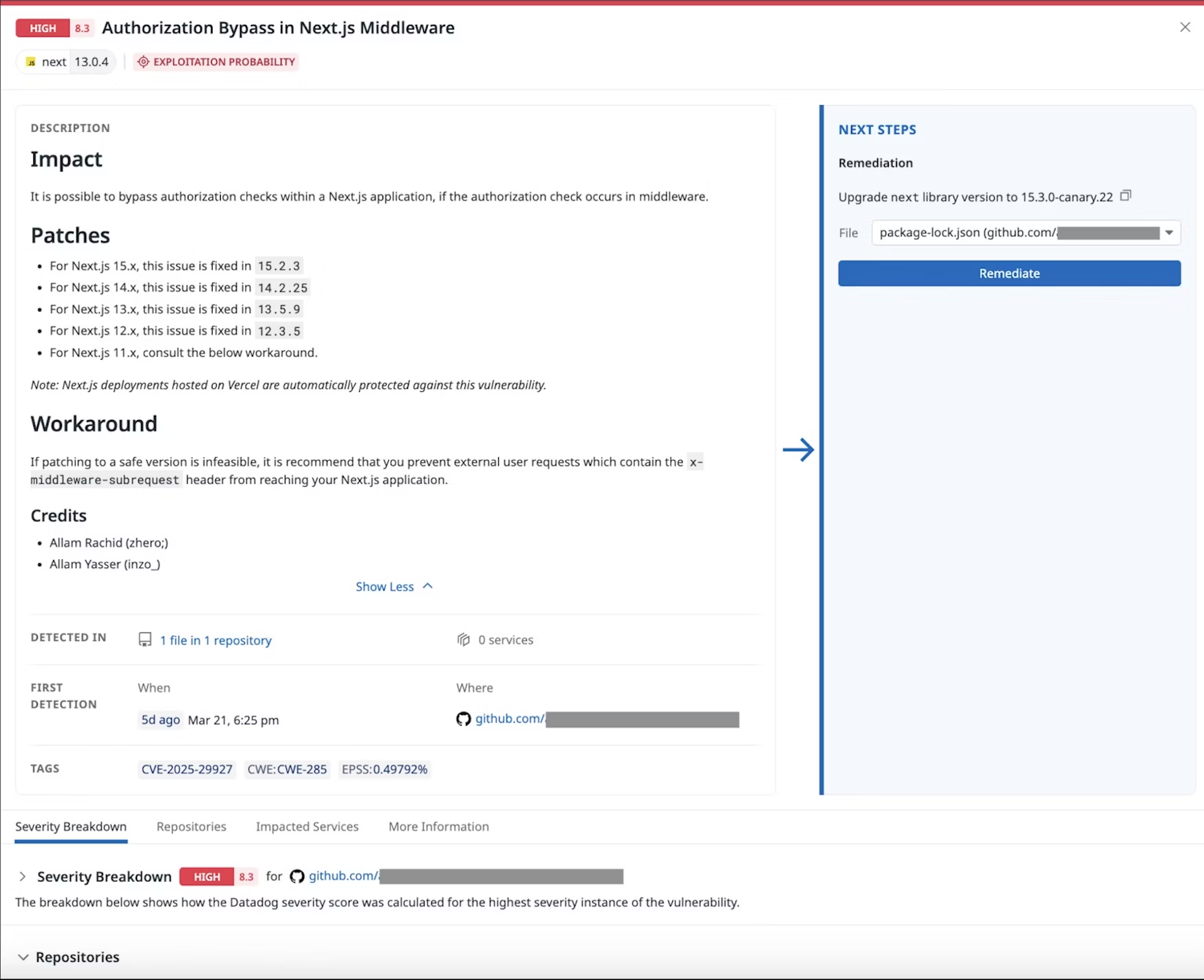
Understanding CVE-2025-29927
The Next.js Middleware Authorization Bypass Vulnerability
Understanding CVE-2025-29927
Key Points and Observations:
- Advisory Date: March 21, 2025
- CVE ID: CVE-2025-29927
- Issue: Authorization bypass through a specially crafted HTTP request with the internal header
x-middleware-subrequest - Impact:
- Affects all Next.js versions earlier than:
- 12.3.5 for 12.x
- 13.5.9 for 13.x
- 14.2.25 for 14.x
- 15.2.3 for 15.x
- Allows skipping of critical middleware security checks
- Can expose administrative routes and sensitive content
- Affects all Next.js versions earlier than:
- Severity: High, due to ease of exploitation and potential consequences
How to Know If You’re Vulnerable:
You are vulnerable if:
- Your deployment is self-hosted and uses
next startwith theoutput: standaloneconfig. - You rely on middleware for essential security/authentication logic.
- Your application runs on an unpatched version of Next.js:
< 12.3.5,< 13.5.9,< 14.2.25, or< 15.2.3
Check Your Version
1
2
3
npm list next
# or
yarn list next
If the version is earlier than the patched versions listed above, immediate remediation is required.
Not Affected If:
- Hosted on Vercel
- Hosted on Netlify
- Deployed as static exports (middleware not executed)
How to Remediate Affected Applications
1. Upgrade Next.js
1
2
3
npm install next@latest
# or
yarn upgrade next@latest
2. Temporary Mitigation (If Upgrade Not Feasible)
- Drop or reject requests that include the
x-middleware-subrequestheader using your web server or proxy.
3. Review Middleware Logic
- Reinforce critical security checks beyond middleware.
- Add redundancy in validation layers.
Background on the Vulnerability
- Middleware in Next.js manages authentication, logging, and security enforcement.
x-middleware-subrequestis a special internal header used by Next.js to track internal requests and avoid recursion.- Exploitation arises when this header is forged by an attacker to bypass middleware logic.
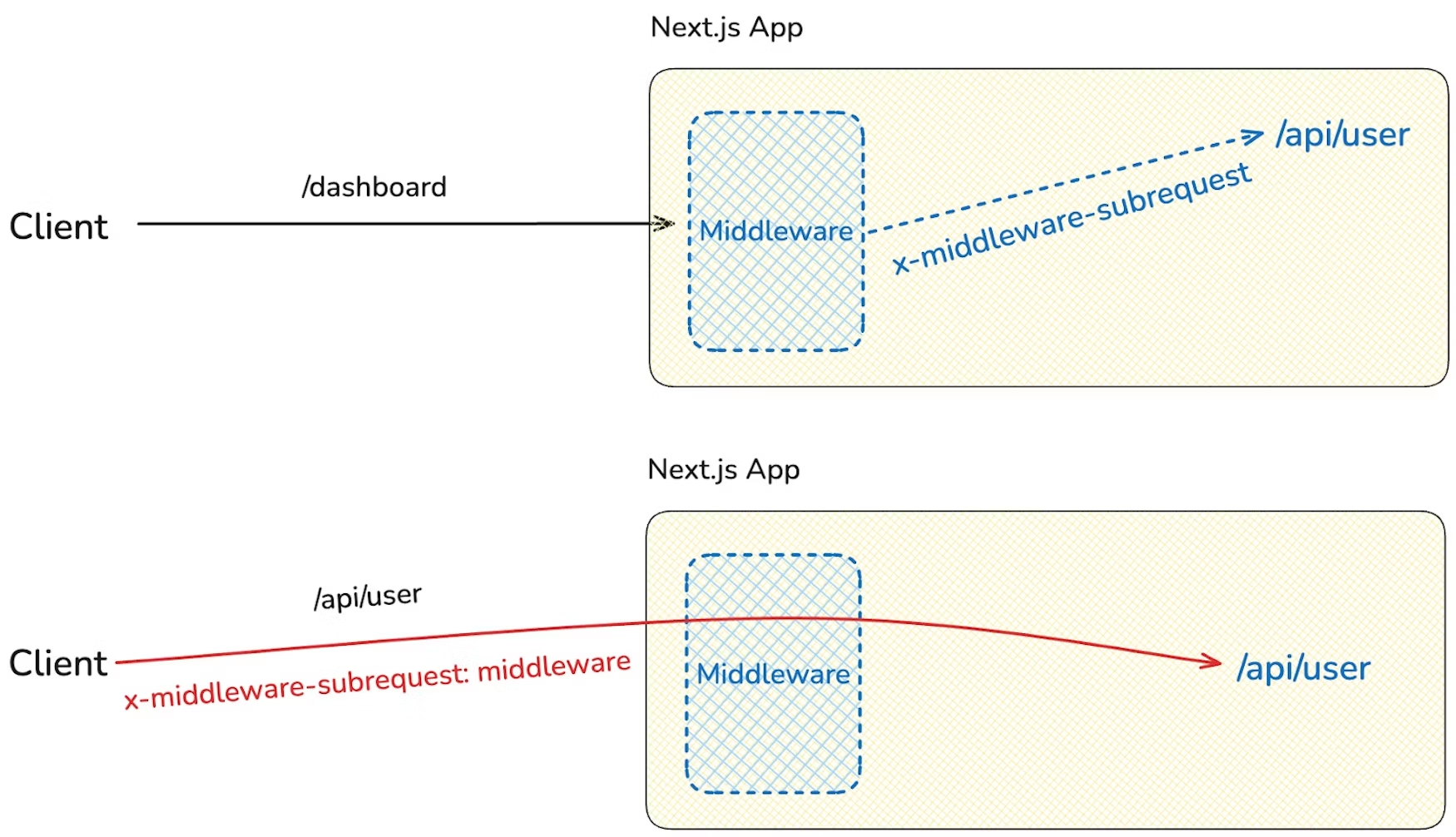
Exploitation Method
- An attacker sends a request to a protected path (e.g.,
/admin) with the forged header:
1
2
3
GET /admin HTTP/1.1
Host: vulnerable-site.com
x-middleware-subrequest:middleware
- In Next.js 15.x, there’s a recursion limit (
MAX_RECURSION_DEPTH = 5). - This can be exploited as well:
1
2
3
GET /admin HTTP/1.1
Host: vulnerable-site.com
x-middleware-subrequest:middleware:middleware:middleware:middleware:middleware
In-the-Wild Observed Exploitation:
Scanning Activity:
- Observed scans are currently low-volume and mostly ineffective.
- Many payloads include paths like:
middlewaresrc/middlewarepages/_middleware
IP Addresses Seen in at Least 5 Environments:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
134.122.111.207
139.162.130.199
139.162.154.240
139.162.171.103
139.162.172.244
139.162.189.169
172.104.149.38
172.104.153.103
172.104.153.129
172.104.153.227
172.104.153.232
172.104.153.235
172.104.153.246
172.104.235.170
172.104.235.194
172.104.235.232
172.104.235.237
172.104.235.59
172.104.245.212
172.105.70.14
172.105.70.162
172.105.70.18
172.105.70.216
172.105.75.116
172.105.75.218
172.105.75.235
172.105.75.95
192.46.237.147
207.180.202.75
45.79.249.191
45.79.249.36
85.90.244.219
85.90.244.8
User-Agents Seen in at Least 5 Environments:
1
2
3
4
5
6
7
8
9
10
Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:130.0) Gecko/20100101 Firefox/130.0
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:137.0) Gecko/20100101 Firefox/137.0
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:86.0) Gecko/20100101 Firefox/86.0
python-requests/2.28.1
How Datadog Can Help:
Code Security:
- Use Code Security Vulnerabilities to identify vulnerable services with:
1
status:Open cve:CVE-2025-29927 is_publicly_accessible:"Accessible"
- Prioritize patching public-facing services.
Application Security Management (ASM):
- Enable WAF rule:
Exploit attempt for Next.js Middleware Exploit (CVE-2025-29927)
Conclusion
This vulnerability demonstrates the critical need for:
- Regularly updating dependencies
- Avoiding over-reliance on middleware for security
- Employing defense-in-depth strategies
Patch CVE-2025-29927 immediately for publicly exposed Next.js services to mitigate risk.
This post is licensed under CC BY 4.0 by the author.