The New Threat Landscape: A Deep Dive into the OWASP Top 10 2025
An in-depth analysis of the OWASP Top 10 for 2025, highlighting new categories, shifts in vulnerability rankings.
The OWASP Top 10 is the industry’s compass, guiding us through the shifting sands of web application security. The 2025 edition has just dropped, and it’s a significant update. Forged from data on over 2.8 million applications and a vital community survey, this list paints a vivid picture of our modern attack surface.
This isn’t just a reshuffle. We have two brand-new categories and a major consolidation, all driven by a powerful focus on the root cause of vulnerabilities, not just their symptoms.
Whether you’re studying the field or hardening enterprise systems, this is what you need to know.
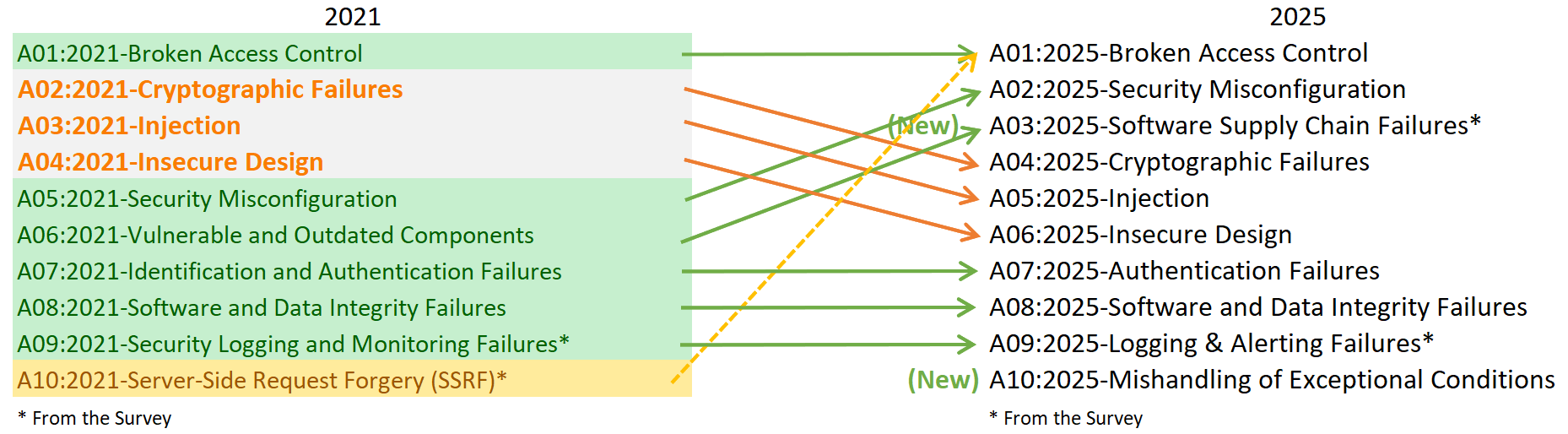
The 2025 OWASP Top 10: The Detailed Breakdown
1. A01:2025 - Broken Access Control
(Maintains #1 Spot)
Imagine a hotel key card that opens your room… but also the manager’s office and your neighbor’s suite. This is the essence of Broken Access Control, and it remains the most critical and prevalent web vulnerability. It represents failures in enforcing who can do what. The most significant change here is the formal consolidation of Server-Side Request Forgery (SSRF). This move confirms that forcing a server to make requests on your behalf (e.g., to internal-only APIs or cloud metadata services) is now fundamentally seen as an access control failure.
2. A02:2025 - Security Misconfiguration
(Up from #5)
This category, which rocketed from #5 to #2, is the digital equivalent of leaving your front door wide open. It covers everything from default admin:admin passwords to public-by-default cloud storage buckets. Its sharp rise reflects our increasingly complex tech stacks. In a world of intricate YAML files, cloud IAM policies, and Kubernetes configs, a single typo or forgotten setting can expose an entire system. This is the “death by a thousand tiny cuts” vulnerability, and its high prevalence (3.00% of apps) proves it.
3. A03:2025 - Software Supply Chain Failures
(New / Expanded Category)
Think of your application as a meal. You trust the ingredients, but what if an attacker poisoned the flour at the factory? This is a supply chain attack. This category is a major expansion of 2021’s “Vulnerable and Outdated Components.” It’s not just about using outdated libraries from npm or Maven; it’s about the integrity of the entire ecosystem: your build systems, package managers, and dependencies. The report notes this category has the highest average exploit and impact scores—it’s the low-frequency, high-impact risk that keeps CISOs up at night.
4. A04:2025 - Cryptographic Failures
(Down from #2)
This is all about secrets being kept badly. Think of storing passwords in plain text, using old and broken encryption like MD5, or sending sensitive data over an unencrypted http:// connection. Its drop from #2 suggests that modern frameworks are finally providing better, more secure defaults. However, it’s still found in 3.80% of applications. A single failure here—like a hardcoded API key in source code—is still a goldmine for attackers, often leading to a catastrophic data breach.
5. A05:2025 - Injection
(Down from #3)
This is the classic “tricking the application” attack. You provide data that the app thinks is a simple username, but it’s actually a malicious command. This includes the infamous SQL Injection (tricking the database into dumping its secrets) and Cross-site Scripting (XSS) (injecting code that runs in other users’ browsers). While modern ORMs have helped mitigate classic SQLi, this category is down, not out. The attack surface has just shifted to OS command injection in microservices, NoSQL injection in cloud databases, and complex DOM-based XSS in single-page applications.
6. A06:2025 - Insecure Design
(Down from #4)
This is a blueprint-level problem. If you build a bank vault with a thin drywall ceiling, it doesn’t matter how strong the door is. This category represents flaws in business logic that a scanner can never find. For example, a password reset feature that only requires an email address. The code might be perfect, but the process is fundamentally insecure. This is the flag-bearer for “shifting left” and integrating Threat Modeling—thinking like an attacker before a single line of code is written.
7. A07:2025 - Authentication Failures
(No Change)
Holding steady at #7, this is all about proving who you are. It includes allowing “brute-force” attacks (letting an attacker guess a password millions of times), not having multi-factor authentication (MFA), or allowing weak passwords. The report credits the increased use of standardized frameworks (like OAuth2 and OIDC) for helping. The risk now is more subtle, lying in the flawed implementation of these complex protocols, such as a misconfigured JSON Web Token (JWT).
8. A08:2025 - Software or Data Integrity Failures
(No Change)
This category is about trusting data you shouldn’t, especially when it’s “unpacked.” The most famous example is Insecure Deserialization. An application takes a bundle of data, “unpacks” it, and trusts it completely. An attacker can craft a malicious ‘bundle’ that, when unpacked, becomes a command to “give me a reverse shell.” This is a close cousin to A03 (Supply Chain), but it focuses on the runtime integrity of data and code, not just its source.
9. A09:2025 - Logging & Alerting Failures
(No Change)
If someone breaks into your house but your security camera isn’t recording, did it even happen? Worse, what if it is recording, but no one ever watches the tape, and you don’t get an alarm on your phone? This is that problem. This category, again voted in by the community, highlights a critical truth: logging without effective alerting is useless. Prevention eventually fails, making detection and response (D&R) vital. Logs that just fill up a disk are a liability; logs that trigger an actionable alert are a defense.
10. A10:2025 - Mishandling of Exceptional Conditions
(New Category)
This is a fantastic brand-new category that focuses on what happens when your application panics. When an error occurs, does it ‘fail-safe’ (like locking a door) or ‘fail-open’ (like unlocking all the doors)? This category covers a wide range of logic-based bugs: verbose error messages that leak server info, flaws where an unexpected value (like a negative number in a shopping cart) breaks the system, and any other failure to handle the “unhappy path” securely.
Final Thoughts
The 2025 OWASP Top 10 is a clear call to action. The focus is decisively shifting from simple, code-level bugs to broader, more systemic issues: Supply Chains (A03), Configurations (A02), and Design (A06).
Use this as your guide to understand the modern threat landscape and to champion a more resilient, defense-in-depth security posture in your work and research.