OWASP TOP 10
A List of Top Ten web vulnerabilities Listed by OWASP(2021)
What is OWASP TOP 10?
The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. 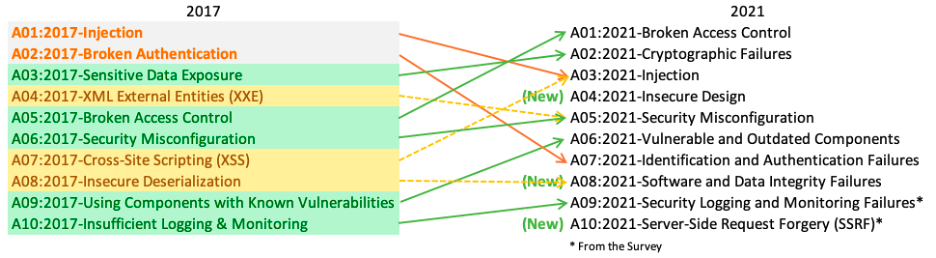
OWASP Top 10 for 2021: Detailed Explanation of Vulnerabilities
1. A01:2021 - Broken Access Control
Broken access control occurs when applications fail to enforce proper restrictions on user permissions. Attackers exploit these vulnerabilities to access unauthorized data or perform unauthorized actions. Common examples include bypassing access control checks, modifying URL parameters to access restricted resources, or escalating privileges. The high frequency of these vulnerabilities—affecting 94% of tested applications—highlights their pervasiveness. Developers often fail to validate user roles or implement least privilege principles, leaving sensitive resources exposed. Mitigation involves robust server-side access control checks, consistent enforcement of policies, and automated testing to identify missing or broken controls during development.
2. A02:2021 - Cryptographic Failures
Cryptographic failures stem from improper implementation or use of encryption. Formerly labeled as “Sensitive Data Exposure,” this category now focuses on weaknesses in cryptography that lead to data compromise. Issues like weak encryption algorithms, insecure key storage, and improper certificate validation are common. For example, using outdated encryption methods like MD5 or improperly securing API keys can allow attackers to decrypt sensitive data. Mitigation strategies include employing modern encryption standards, managing keys securely using tools like Hardware Security Modules (HSMs), and validating cryptographic implementations. This ensures sensitive data remains secure during storage and transmission.
3. A03:2021 - Injection
Injection vulnerabilities occur when untrusted input is executed as code or a command by an application. Common types include SQL, LDAP, and OS command injection. These attacks allow attackers to manipulate queries, retrieve sensitive information, or execute arbitrary commands. For example, a vulnerable SQL query might allow attackers to extract entire databases using simple payloads like ' OR '1'='1. Injection flaws can lead to severe impacts, including data breaches or system compromises. Mitigation includes input validation, parameterized queries, and avoiding direct command execution. Integrating secure coding practices and automated scanning tools during development is also crucial.
4. A04:2021 - Insecure Design
Insecure design emphasizes risks introduced during the architecture or planning stages of application development. Unlike implementation bugs, these vulnerabilities arise from poorly considered security requirements. Examples include applications lacking proper threat modeling, weak authentication flows, or insecure default configurations. These flaws make applications inherently vulnerable, even before deployment. Mitigating insecure design requires a shift-left approach—embedding security in the design phase through threat modeling, secure design principles, and reference architectures. This category highlights the importance of proactively addressing security concerns before development begins, minimizing the chances of fundamental vulnerabilities.
5. A05:2021 - Security Misconfiguration
Security misconfigurations occur when application or server settings inadvertently expose the system to threats. Examples include default admin credentials, overly verbose error messages, or leaving unnecessary services enabled. With 90% of applications tested showing misconfigurations, this issue is widespread, exacerbated by the complexity of modern software ecosystems. Misconfigurations like unpatched servers or improperly configured cloud storage can lead to breaches or data leaks. Mitigation involves regular configuration reviews, automated compliance tools, and ensuring that systems adhere to security best practices. Establishing secure defaults and enforcing configuration baselines across environments can significantly reduce risks.
6. A06:2021 - Vulnerable and Outdated Components
This category focuses on the use of libraries, frameworks, or software components with known vulnerabilities. Organizations often fail to keep track of dependencies, resulting in outdated or unsupported components in production systems. Attackers exploit these vulnerabilities to gain unauthorized access or control. For instance, using an outdated version of a web framework could expose applications to known exploits. Mitigation requires maintaining an updated inventory of dependencies, monitoring for updates, and implementing automated dependency management tools. Regular vulnerability scanning and using security-focused dependency scanners ensure risks are minimized.
7. A07:2021 - Identification and Authentication Failures
Formerly called “Broken Authentication,” this category highlights weaknesses in managing user identities and authentication mechanisms. Examples include weak password policies, flawed session management, or insecure token handling. Attackers can exploit these flaws to impersonate users or escalate privileges. For example, failure to invalidate session tokens after logout allows attackers to hijack active sessions. Mitigation involves adopting multi-factor authentication (MFA), enforcing strong password requirements, and properly managing session tokens. Using standardized authentication frameworks and libraries reduces the risk of implementation errors.
8. A08:2021 - Software and Data Integrity Failures
This category addresses risks related to unverified software updates, critical data, and CI/CD pipelines. Attackers exploit these weaknesses to inject malicious payloads or alter data. Examples include dependency confusion attacks or insecure deserialization, where untrusted input is processed as code. Such vulnerabilities can lead to backdoors in software or compromised application behavior. Mitigation requires verifying the integrity of software and data using techniques like digital signatures, securing CI/CD pipelines, and validating inputs during deserialization. Organizations should also adopt secure software supply chain practices to reduce risks.
9. A09:2021 - Security Logging and Monitoring Failures
Failures in logging and monitoring result in delayed detection of breaches or system compromises. Applications often lack sufficient logging, fail to monitor critical activities, or miss sending alerts during suspicious events. For example, inadequate logging might leave a brute force attack undetected until it’s too late. Mitigation includes implementing centralized logging, enabling alert systems for anomalous activities, and regularly reviewing logs for suspicious patterns. Ensuring comprehensive coverage for all critical events enhances visibility and supports forensic investigations after an incident.
10. A10:2021 - Server-Side Request Forgery (SSRF)
SSRF vulnerabilities allow attackers to manipulate server-side requests to access unauthorized resources. For example, an attacker could exploit SSRF to access internal APIs or metadata services in cloud environments. Although less prevalent, the high exploit and impact potential make it a significant risk. Mitigation involves validating and sanitizing user inputs for server-side requests, restricting outgoing network access for servers, and employing allowlists to prevent unauthorized access. Proper implementation of network segmentation can further limit the damage potential of SSRF vulnerabilities.
By addressing these vulnerabilities with a proactive and systematic approach, organizations can significantly enhance their application security posture.