Weaponized PDF
Hackers Using Weaponized PDF To Deliver Remcos RAT Malware on Windows
Researchers at Trustwave SpiderLabs has uncovered a sophisticated malspam campaign distributing the notorious RemcosRAT malware on windows.
The campaign leverages a deceptive fake payment notice disguised as a SWIFT copy to trick victims into downloading a malicious PDF, ultimately leading to the deployment of the remote access trojan (RAT).
Technical Analysis
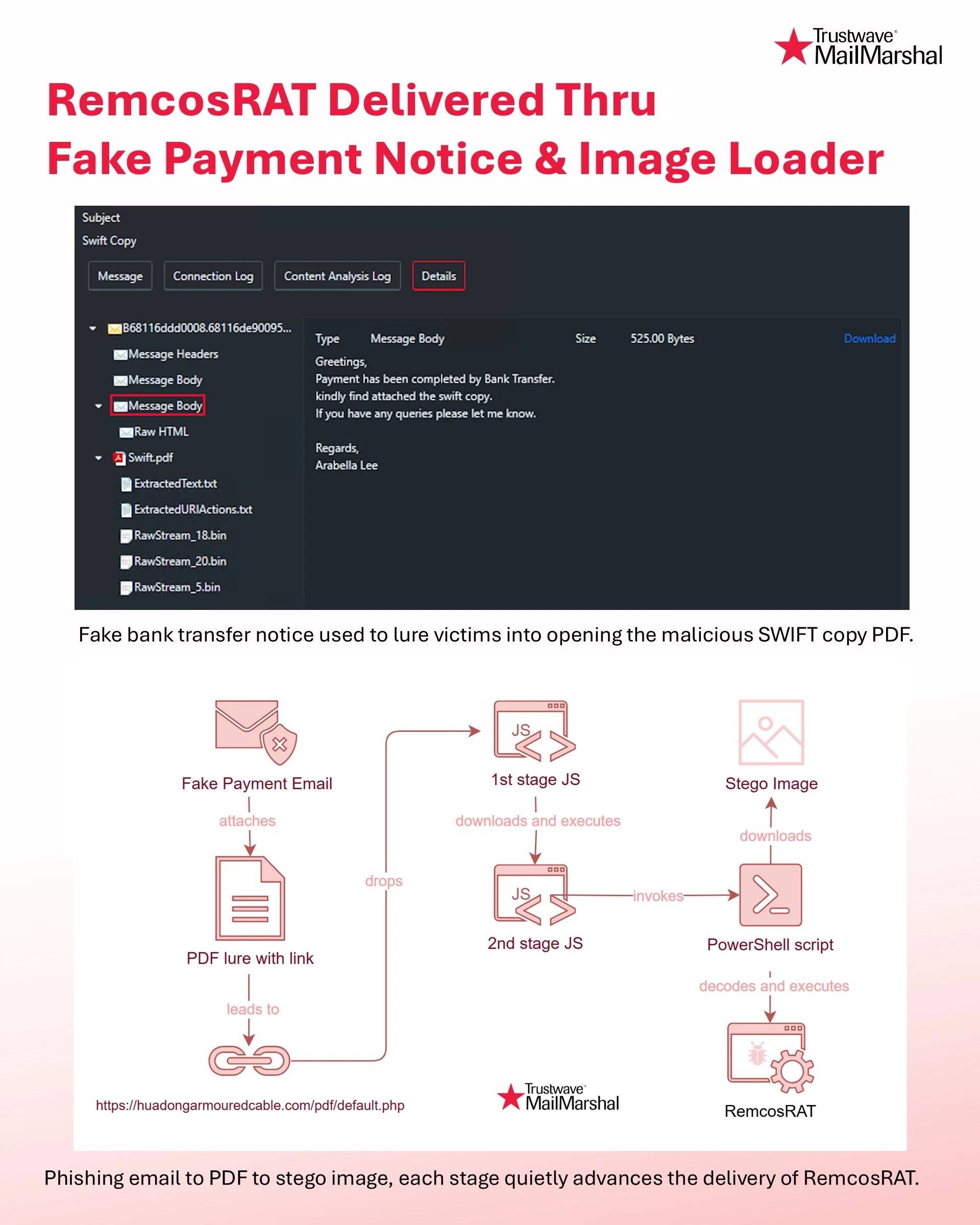
The campaign begins with a phishing email that attaches a PDF file contains a malicious link, specifically pointing to malicious webpage: https://huadongarmouredcable.com/pdf/default.php.
This link serves as the entry point for the attack, luring victims into a multi-stage infection process designed to deliver RemcosRAT, a malware known for its ability to remotely control infected systems.
The attack unfolds in several carefully orchestrated steps. The initial PDF link leads to the download and execution of a first-stage JavaScript (JS) file. This script then fetches a second-stage JS file, which in turn invokes a PowerShell script.
The PowerShell script downloads an image file that appears harmless but is embedded with the RemcosRAT payload, concealed using steganography a technique that hides malicious code within the image.
Once decoded and executed, the malware establishes a connection to a command-and-control (C2) server, giving attackers remote access to the victim’s system.
The email identified in the campaign, as shown in a screenshot provided by Trustwave MailMarshal, includes a message body with a fake payment notice.
The message, titled “SWIFT Copy,” claims to be a legitimate bank transfer confirmation and urges the recipient to open the attached PDF for further details.
The email’s metadata reveals a message body size of 525 bytes, with the sender posing as “Arabella Lee” and the content designed to appear authentic with a polite closing: “If you have any queries, please let me know.”
SpiderLabs also shared indicators of compromise (IoCs) to help organizations detect and block the threat. The malicious URLs involved include:
1
2
3
4
hxxps://huadongarmouredcable.com/pdf/default.php
hxxp://whiteafrica.lovestoblog.com/arquivo_8c092766561d46738b51ca112074f5d9.txt
hxxp://whiteafrica.lovestoblog.com/arquivo_ba000f161f624940a1b722da3c40e06b.txt
hxxps://archive.org/download/new_image_20250413/new_image.jpg
Additionally, the C2 server used in this campaign operates at ` tcp://www.rickscottflorida.com:2404.`
The report also lists specific file hashes associated with the malware, including 3f83dc5091032487182bba6727eb9b8d and 2f12470db4f787de480173d34fd69d78e53f265e229d9ee93cc278d7fe1ecfb9, as well as a file pattern Swift[0-9]{5}.js.
The use of steganography to conceal the payload within an image file highlights the advanced tactics employed by the attackers to evade detection.
This campaign demonstrates a clear evolution in malware delivery methods, combining social engineering with obfuscated scripts and hidden payloads to bypass traditional security measures.
Organizations are urged to update their security protocols, monitor for the provided IoCs, and educate employees about the risks of opening attachments or clicking links in unexpected emails.
This discovery adds to the growing list of Remcos RAT campaigns, a malware strain known for its versatility and use in espionage, data theft, and other malicious activities.
As cybercriminals continue to refine their techniques, cybersecurity experts stress the need for robust defenses and proactive threat hunting to mitigate such risks.