XZ Utils Backdoor
Everything You Need to Know about XZ Utils Backdoor
Introduction
CVE-2024-3094 is a critical vulnerability discovered in the open-source library XZ Utils, caused by malicious code introduced by one of its maintainers. Initially reported as an SSH authentication bypass, further analysis has revealed that the backdoor enables Remote Code Execution (RCE).
The threat actor behind this exploit spent nearly two years gaining trust in the open-source community before inserting the backdoor. This type of long-term infiltration is typically associated with state-sponsored actors, though no definitive attribution exists yet.
Executive Summary
- CVE-2024-3094 is a malicious backdoor introduced into XZ Utils by a maintainer.
- The backdoor initially allowed SSH authentication bypass but later analysis confirmed it enables Remote Code Execution (RCE).
- The attacker gained repository maintainership by social engineering tactics.
- The backdoor is present in XZ Utils versions 5.6.0 and 5.6.1.
- The recommended mitigation is to downgrade to a secure version (5.4.6 or earlier).
- We discuss detection methods and threat-hunting strategies to identify and mitigate the risk.
Backstory
What is XZ Utils?
XZ Utils (formerly LZMA Utils) is a set of compression tools used extensively in Linux distributions and open-source projects. Its core library, liblzma, is widely integrated into system utilities, package managers, and compression tools.
The Attacker’s Strategy
Around two years ago, a developer under the alias Jia Tan began contributing to XZ Utils. Over time, they gained commit access and eventually release manager rights. Their infiltration method included:
- Contributing bug fixes and minor improvements.
- Creating fake accounts to pressure maintainers with feature requests and bug reports.
- Gaining enough credibility to be entrusted with release management.
In 2023, the attacker introduced a complex and stealthy backdoor in version 5.6.0 of XZ Utils, which became active in Linux distributions.
The Backdoor Mechanism
How It Works
The backdoor is not visible in the public GitHub repository but was included in source code tarball releases. The attack consists of multiple components:
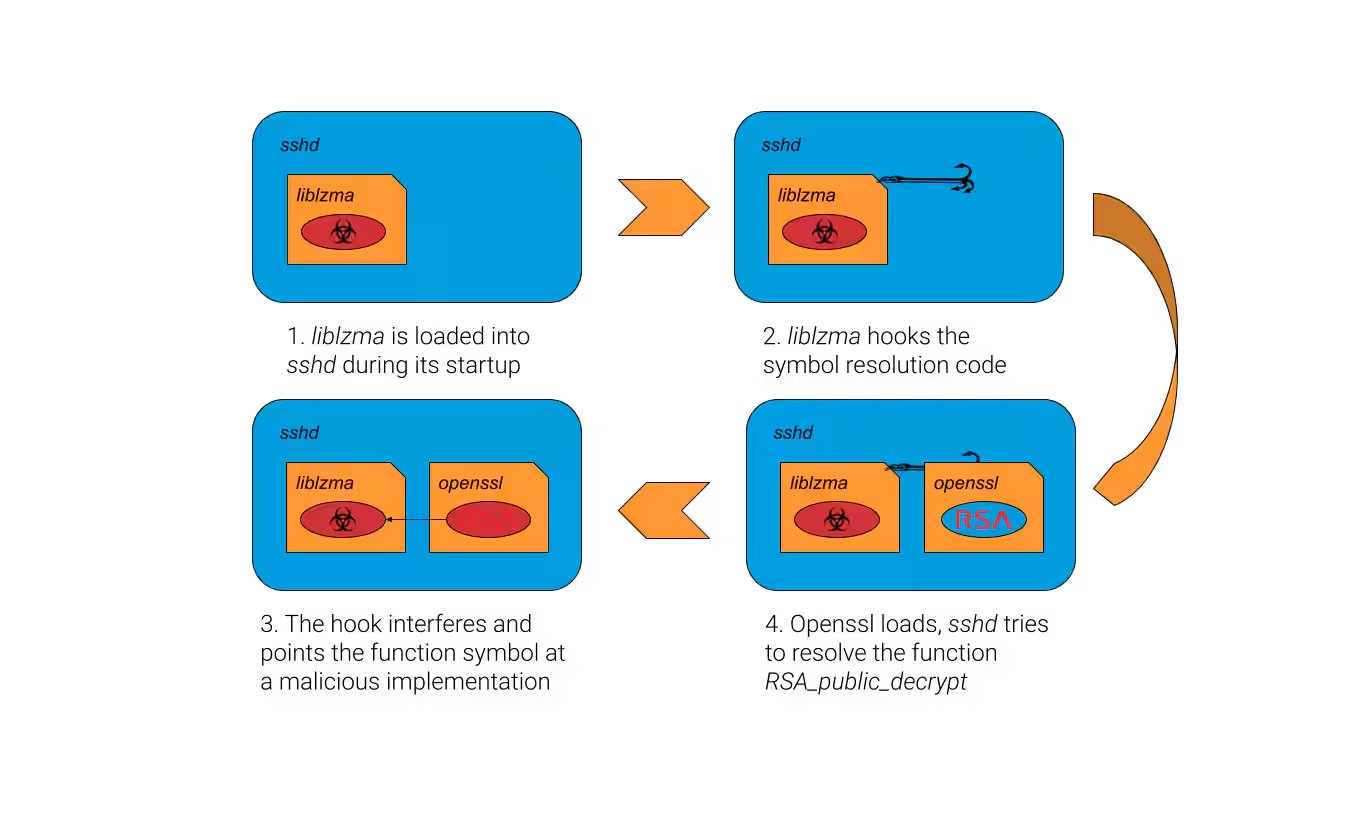
1. IFUNC-Based Symbol Hijacking
- The attacker modified the linker (IFUNC) mechanism to hijack function resolution.
- The backdoor intercepts RSA_public_decrypt() in OpenSSH.
2. Obfuscated Components in Test Files
- Malicious shared objects were hidden in test files.
- A script extracts these objects during the build process.
- A secondary script disables Landlock, a security mechanism that restricts process privileges.
3. Multi-Stage Execution Chain
1
2
3
4
1. The script `build-to-host.m4` decodes `bad-3-corrupt_lzma2.xz` into a Bash script.
2. The Bash script decodes another test file, `good-large_compressed.lzma`, into another script.
3. The second script extracts a shared object (`liblzma_la-crc64-fast.o`).
4. This object is injected into `liblzma`, hijacking OpenSSH authentication.
- The backdoor executes system(), allowing the attacker to run arbitrary commands before authentication.
Potential Impact
If left undetected, this backdoor could have led to one of the most severe security breaches in Linux history, surpassing even SolarWinds.
Who is Vulnerable?
Any Linux system running an affected version of XZ Utils (5.6.0, 5.6.1) and exposing SSH to the internet is vulnerable. This includes:
- Fedora
- Ubuntu
- Debian
How It Was Discovered
The backdoor was discovered by Andres Freund, who noticed a 500ms latency issue after an XZ update. Upon investigation, he traced the issue back to malicious modifications in liblzma.
Detection & Mitigation
Check Your XZ Utils Version
Run the following command to check the installed version:
1
xz --version
If the version is 5.6.0 or 5.6.1, immediately downgrade to 5.4.6.
List Affected Instances
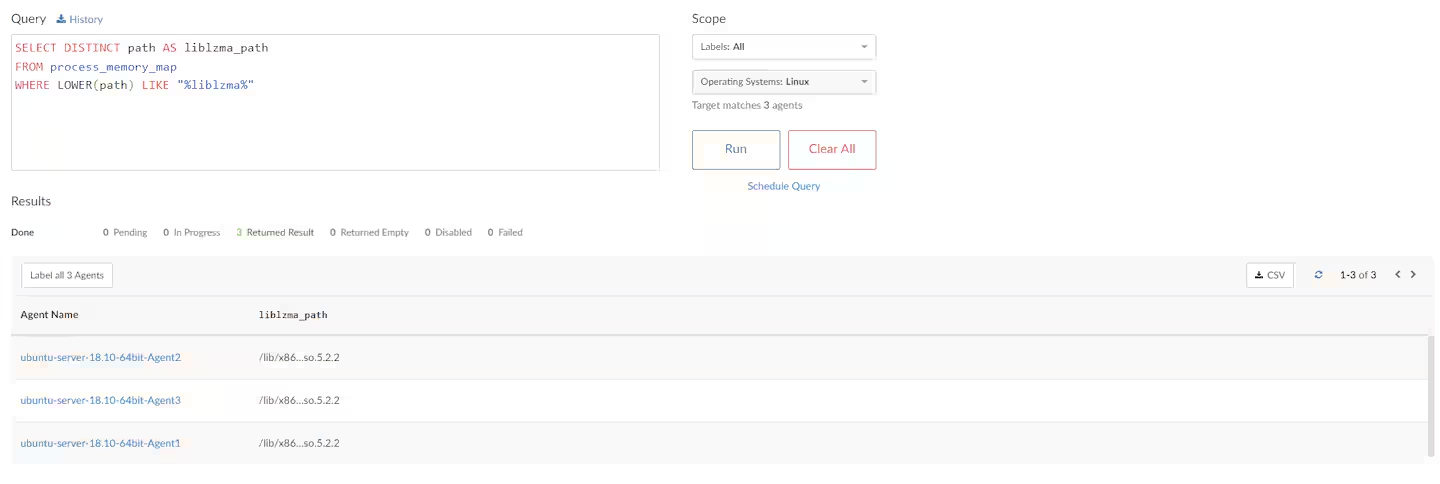
Use Akamai Guardicore Segmentation Insight to find running instances of the vulnerable library:
1
2
3
SELECT DISTINCT path AS liblzma_path
FROM process_memory_map
WHERE LOWER(path) LIKE "%liblzma%";
For package managers:
1
2
3
4
5
6
7
8
9
SELECT name AS vulnerable_item, 'DEB' AS type, version
FROM deb_packages
WHERE LOWER(name) LIKE '%xz-utils%' OR LOWER(name) LIKE '%liblzma%'
UNION
SELECT name AS vulnerable_item, 'RPM' AS type, version
FROM rpm_packages
WHERE LOWER(name) LIKE '%xz-utils%' OR LOWER(name) LIKE '%liblzma%';
Mitigation Steps
1. Downgrade to a Safe Version
1
sudo apt-get install --reinstall xz-utils=5.4.6
For Fedora/Debian:
1
yum downgrade xz
2. Hunt for Anomalous SSH Behavior
Since the backdoor executes commands directly from SSH, you can detect suspicious activity by tracking process execution:
1
sudo ausearch -c 'sshd' | grep 'system()'
3. Apply the Kill Switch
Some analyses suggest that the backdoor can be disabled by setting an environment variable:
1
export yolAbejyiejuvnup=Evjtgvsh5okmkAvj
Final Thoughts
The XZ Utils backdoor (CVE-2024-3094) underscores the risk of supply chain attacks in open-source projects. This case highlights the importance of:
- Code auditing and version control for critical infrastructure.
- Behavioral anomaly detection to identify unexpected system calls.
- Community vigilance—this backdoor was caught purely by chance.
Organizations should downgrade immediately, implement process monitoring, and consider sandboxing security-critical libraries to prevent future attacks.